Crypto Bug Bounties: How to Get Started
December 5, 2025

by Coinmetro Editorial Team
December 5, 2025
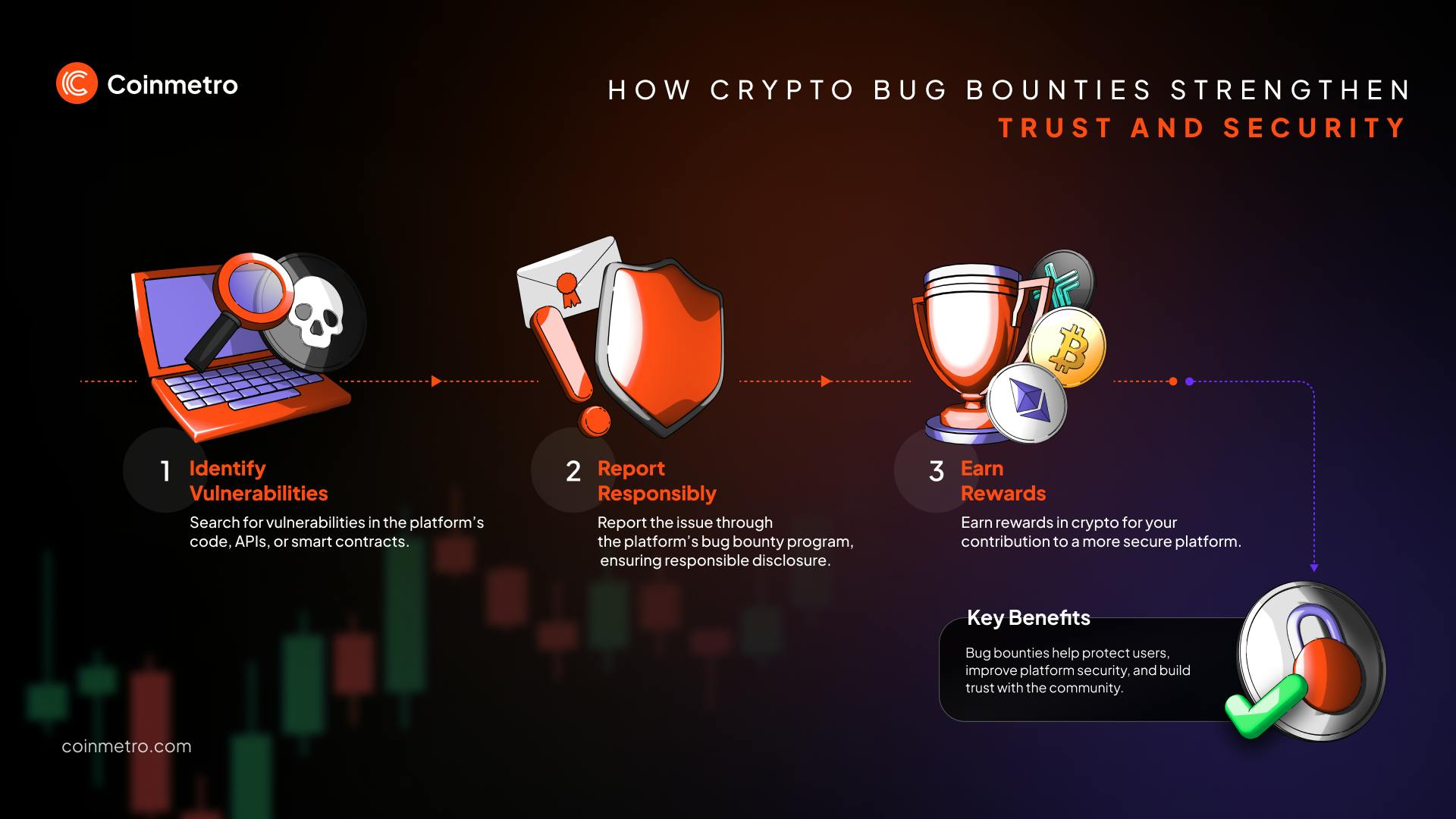
Crypto bug bounties are programs where crypto and blockchain platforms pay people for finding security flaws. This encourages ethical hackers to report problems, allowing companies to fix them before bad actors use them. By looking for issues first, organizations make their platforms safer and more reliable.
Unlike traditional systems, blockchain networks have no central control, making them prime targets for cyberattacks. Bug bounty programs use the global community's skills to spot and fix issues, keeping the network secure.
Some bugs found through such programs have been major. For example, in 2021, a flaw in Poly Network let hackers steal $610 million. They returned the money to highlight the vulnerability. Poly Network then offered a $500,000 reward and invited them to be a "chief security advisor," showing how valuable bug bounties can be.
Ethereum's bug bounty program also helps find and fix security issues. By joining these programs, people help secure the crypto world while earning rewards for their work.
Crypto security protects user funds and keeps platforms reliable. Bug bounty programs let ethical hackers find vulnerabilities. They help exchanges fix issues fast, stopping bad actors from exploiting them.
Exchanges like Coinmetro use these programs to make their platforms safer. We invite experts to test our systems and reward them for finding flaws. This lowers risks and demonstrates our commitment to safeguarding our users.
Bug bounties also build trust by proving that exchanges prioritize security and transparency. They link platforms with cybersecurity experts, making the crypto world safer for everyone.
Bug bounty programs pay participants for finding security flaws. Rewards depend on how serious the problem is. This way, ethical hackers can make good money by finding key issues. Besides money, participants get public praise, boosting their careers in cybersecurity. They also improve their skills by dealing with real challenges.
These programs make crypto platforms safer by catching vulnerabilities early. By fixing problems before hackers can use them, platforms cut down on risks and losses. This protects user funds and builds trust. When users see a focus on security, they feel more confident and loyal.
Bug bounty programs are win-win. Hackers earn rewards and fame while the crypto world becomes stronger and more secure. This helps the industry grow into a safer place for everyone.
Smart Contract Exploits: Smart contracts run on set rules in apps. Bad code may allow hackers to steal funds. Reporting these issues keeps user money safe.
API Vulnerabilities: APIs help systems communicate. Weak authentication or leaks can compromise data. Spotting these keeps systems secure.
Issues with Wallets, Withdrawals, or Deposits: Bugs in wallets or transactions risk fund loss. Quick fixes are needed to keep services running smoothly.
User Interface and Functionality Bugs: UI or function errors can mislead users. Reporting these boosts the platform's safety and usability.
Platforms categorize vulnerabilities based on severity. For example:
Critical Issues: These include exploits that can lead to significant financial loss or data breaches. Rewards are often the highest for these findings.
High-Risk Bugs: Vulnerabilities that disrupt operations or compromise a system's stability fall into this category.
Moderate Issues: These bugs might cause inconveniences without immediate financial or security risks.
Low Priority: Minor glitches, such as typos or small UI errors, typically receive smaller rewards but still contribute to overall platform improvement.
Crypto platforms reward participants based on reported bugs' severity and potential impact. Critical vulnerabilities often yield substantial payouts, while smaller issues earn less. This structure motivates researchers to focus on high-impact vulnerabilities while also addressing minor problems.
By reporting these vulnerabilities, you contribute to the security and reliability of crypto platforms, helping protect users and maintain trust in the ecosystem.
A solid grasp of blockchain principles is essential. It would help if you understood how transactions work, how smart contracts function, and what security measures protect cryptosystems. Familiarity with consensus mechanisms, such as proof-of-work or proof-of-stake, will also help you identify potential vulnerabilities in blockchain platforms.
You’ll need programming skills, particularly in languages like Solidity (for Ethereum smart contracts), Python, or JavaScript. Knowledge of cryptography, hashing algorithms, and cybersecurity frameworks is also critical. Key tools include:
- MythX: Used for analyzing Ethereum smart contracts.
- Burp Suite: Helps test API security and detect vulnerabilities.
- Wireshark: Monitors network traffic for security analysis.
Metasploit: Assists in testing system defenses against simulated attacks.
Several platforms connect ethical hackers with bug bounty programs:
- HackerOne: A popular platform hosting programs from leading crypto companies.
- Bugcrowd: Another top platform featuring cryptocurrency and blockchain-related bounties.
- Immunefi: Specializes in crypto security, offering programs from exchanges and DeFi platforms.
- Cobalt: Focuses on penetration testing and bug bounties for high-tech industries, including blockchain.
By mastering blockchain basics, leveraging the right tools, and joining these platforms, you’ll be well-prepared to participate in bug bounty programs and contribute to the security of the crypto ecosystem.
Protecting Users: Responsible disclosure means telling companies about flaws privately. This keeps users safe by fixing issues before they're exploited. It reduces risks and protects assets.
Fostering Trust: Ethical reporting builds good ties between researchers and platforms. When researchers are professional, companies trust them more. This can lead to bigger rewards, better teamwork, and special program invites.
Submit through Official Channels: Always use the communication methods specified by the bug bounty program, such as secure web portals or designated email addresses.
Avoid Public Sharing Until Resolution: Keep all information confidential until the platform resolves the issue. Premature disclosure can put users and the company at unnecessary risk.
Collaborate with the Platform Team: Work closely with the team to verify the issue and assist in resolving it, if required. This cooperative approach speeds up the process and ensures a stronger outcome.
Responsible disclosure is the backbone of ethical hacking. It fosters a safer crypto ecosystem, builds lasting relationships, and helps researchers make a meaningful impact while earning well-deserved rewards.
Bug bounty programs play a critical role in protecting the cryptocurrency ecosystem. By identifying and reporting vulnerabilities, participants ensure platforms remain secure, and user assets stay protected. These programs reduce the risks of cyberattacks and build trust in cryptocurrency exchanges' safety and reliability.
For individuals, joining bug bounty programs is an opportunity to make a tangible impact while earning meaningful rewards. You contribute to creating a safer crypto space while developing valuable skills and gaining recognition.
Start exploring bug bounty opportunities today and join the effort to secure crypto's future. Together, we can make the ecosystem safer for everyone.
Read More About Crypto Bounties
Join the Coinmetro community on Discord and Telegram, where forward-thinking traders and investors gather to share insights, explore new opportunities, and dive deep into cryptocurrencies. Should you need any help, please contact our world-class Customer Support Team via 24/7 live chat or email at hello@coinmetro.com.
To become a Coinmetro user today, Sign Up now or head to our new Exchange if you are already registered to experience our premium trading platform.
Tags
Related Articles
Regulatory Sandboxes: Fostering Crypto Innovation Within Legal Frameworks
The cryptocurrency industry’s fast rise fuels an important debate. Innovation aims to transform finance, enhancing speed and access. Yet, regulators…
5m

Crypto Options Trading: Strategies and Market Insights
Cryptocurrency markets have rapidly expanded beyond simple buying and selling. One of the most significant developments has been the rise of…
6m

The Rise of Social-Fi: Blending Social Media with Decentralized Finance
In recent years, social media and finance have started to merge, creating Social-Fi. This concept blends the engagement of social platforms with…
6m

DeFi Insurance Platforms to Watch in 2024
Decentralized Finance (DeFi) insurance addresses the growing need for insurance against hacks, smart contract failures, and other DeFi-related risks.…
7m